The device consists of a handheld host and a battery pack. The handheld host is designed with an integrated three-band transmitter and antenna, which can simultaneously generate 2.4GHz/5.8GHz frequency band UAV flight control interference signals and satellite positioning interference signals, by analyzing the UAV’s uplink flight control channel and satellite positioning channel Blocking interference causes the drone to lose flight control instructions and satellite positioning information, making it unable to fly normally. Depending on the design of the drone, it will have control effects such as return, landing and crash.
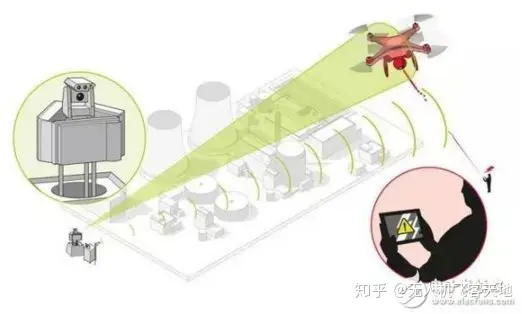
In terms of offensive and defensive posture, there is usually a certain distance between the operator of the drone and the sensitive area that needs to be fortified. The drone takes off from near the operator and then gradually flies towards the fortified area. When a drone arrives near a fortified area and can carry out effective reconnaissance or sabotage activities, the drone’s distance to the fortified area is usually much closer than its distance to the operator.
In the above situation, all uplink signals sent by the operator (sent from the ground to the drone) will be weaker due to the distance. Using the same power, the defender’s signal will be stronger than the operator’s due to being closer to the drone. Defenders will also receive stronger downward signals than manipulators. However, the goal of defending the downlink signal is to prevent the operator from receiving it. At this time, the distance from the drone to the operator is about the same as the distance from the defender to the operator. Therefore, blocking the downlink signal does not take advantage of the terrain.
From the above analysis, we can see that it is more beneficial to interfere with the uplink signal. It just so happens that the uplink signal is usually a remote control signal, which is directly related to the control of the drone. If the uplink signal is interfered with, the drone will lose immediate control and can only operate according to the steps preset by the program (usually landing or hovering). Downlink signals are mainly telemetry and images. Although there may be sensitive information, they are less important than control signals. In addition, defenders do not have an advantage in situation and usually adopt a laissez-faire attitude towards downlink signals.
GPS relies on medium-orbit satellites. In layman’s terms, the signal has traveled tens of thousands of kilometers to reach the earth’s surface, and is already very weak. So it is relatively easy to jam the GPS signal when the drone is very close to the defender. If you want to deceive it, you need to use more complicated means to simulate GPS satellites, which will be much more difficult.

At present, radio communication technology is mostly used to control UAVs. By transmitting high-power interference signals to the target UAV and suppressing the control signals, the UAV can be forced to land or return on its own.
The United States has taken advantage of this principle. This gun installs an electronic jammer on the frame of the rifle. Once the trigger is pulled, the jammer will transmit a full-band jamming signal to the drone, causing the drone to escape from the operator’s control and fail to receive the control signal. Automatically land to the ground.
Once a drone’s signal is confused, it usually has three options: drop to the ground, return to the operator, or descend smoothly. The effective range of this rifle reaches 500 to 2000 meters.
At present, under normal circumstances, the vast majority of consumer drones will prefer GPS navigation for flight control, and civilian GPS signals are unencrypted, which leaves room for use.
The main principle of GPS spoofing is to send false geographical location coordinates to the drone’s control system, thereby controlling the navigation system and inducing the drone to fly to the wrong location. GPS signals can be generated by a generator, or they can be recorded and then played back. Since drones always receive GPS signals based on the signal source with the strongest signal, as long as the artificial GPS signal on the ground is strong enough, it can cover the real GPS signal transmitted from space, thereby deceiving the drone. GPS receiving module.
At present, various countries have set up no-fly zones in core areas. Many drone manufacturers have set it up in the built-in firmware of drones. Drones cannot take off within the no-fly zone, and even if they reach the no-fly zone, they will Automatic landing. Therefore, as long as the artificial GPS signal on the ground simulates the geographical location as the coordinates of the no-fly zone, the drone can be forced to land on its own.

Nowadays, most of the control signals used by drones are in conventional civilian frequency bands such as 1.2GHz, 2.4GHz, and 5.8GHz. With the rapid development of open source hardware such as Arduino and Raspberry Pi and the popularity of software-defined radio (SDR) technology, ordinary enthusiasts You can also use hardware purchased from the Internet and software source code obtained from forums to simulate a remote control and send control signals to the drone, and overwrite the signals of the real remote control, thereby obtaining control of the drone.
In order to facilitate users to control using mobile devices such as mobile phones and tablets, many drones directly use Wi-Fi for interaction. In this way, some hacking techniques that are already mature on the Internet can be directly applied to drones.
For example, through the open port or password guessing in the drone control system, you can enter the control system to control the drone. Samy Kamkar, the legendary hacker who developed the “Samy Worm”, used this principle to write a drone hijacking software called “SkyJack” and installed the software on specially configured drones. In the aircraft, SkyJack flies through the air and looks for other drones within Wi-Fi range, then hacks into the drone and takes control.
Professionals engaged in anti-drone applications in the industry said that the current domestic anti-drone technology is still in the exploratory stage. Radio hijacking technology is difficult to implement because various drone manufacturers encrypt radio signals, while hacking technology is difficult to implement due to the encryption of radio signals by various drone manufacturers. The threshold is high and it is difficult to commercialize, so the technology currently used is mainly based on interference blocking.